Penetration Testing Services
Detect vulnerabilities before the hackers do
Trusted by Top Industry Leaders


Benefits of working with CYBRI
U.S.-Based Red Team
All CYBRI Red Team members are U.S.-based, experienced, and highly certified penetration testers.
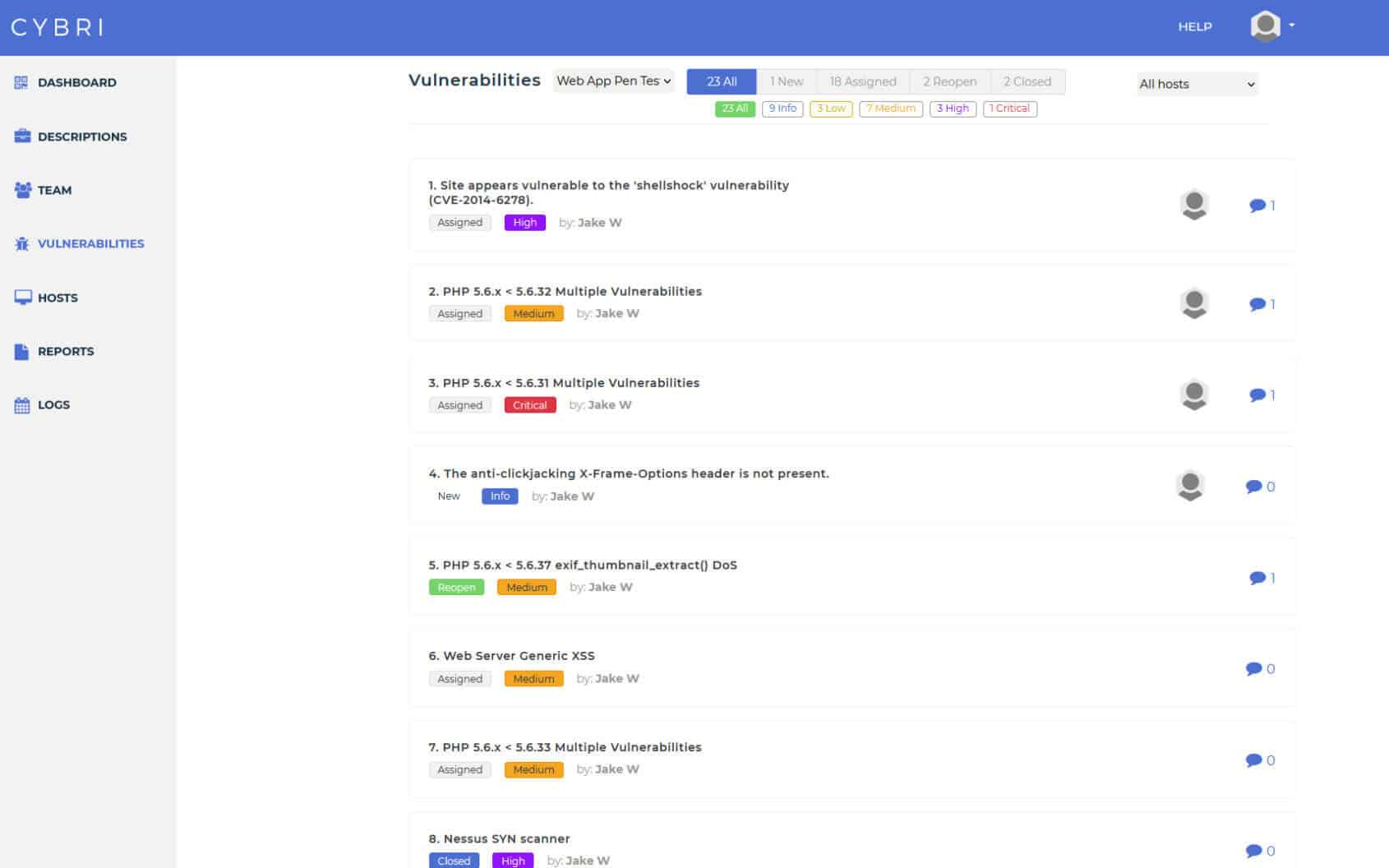
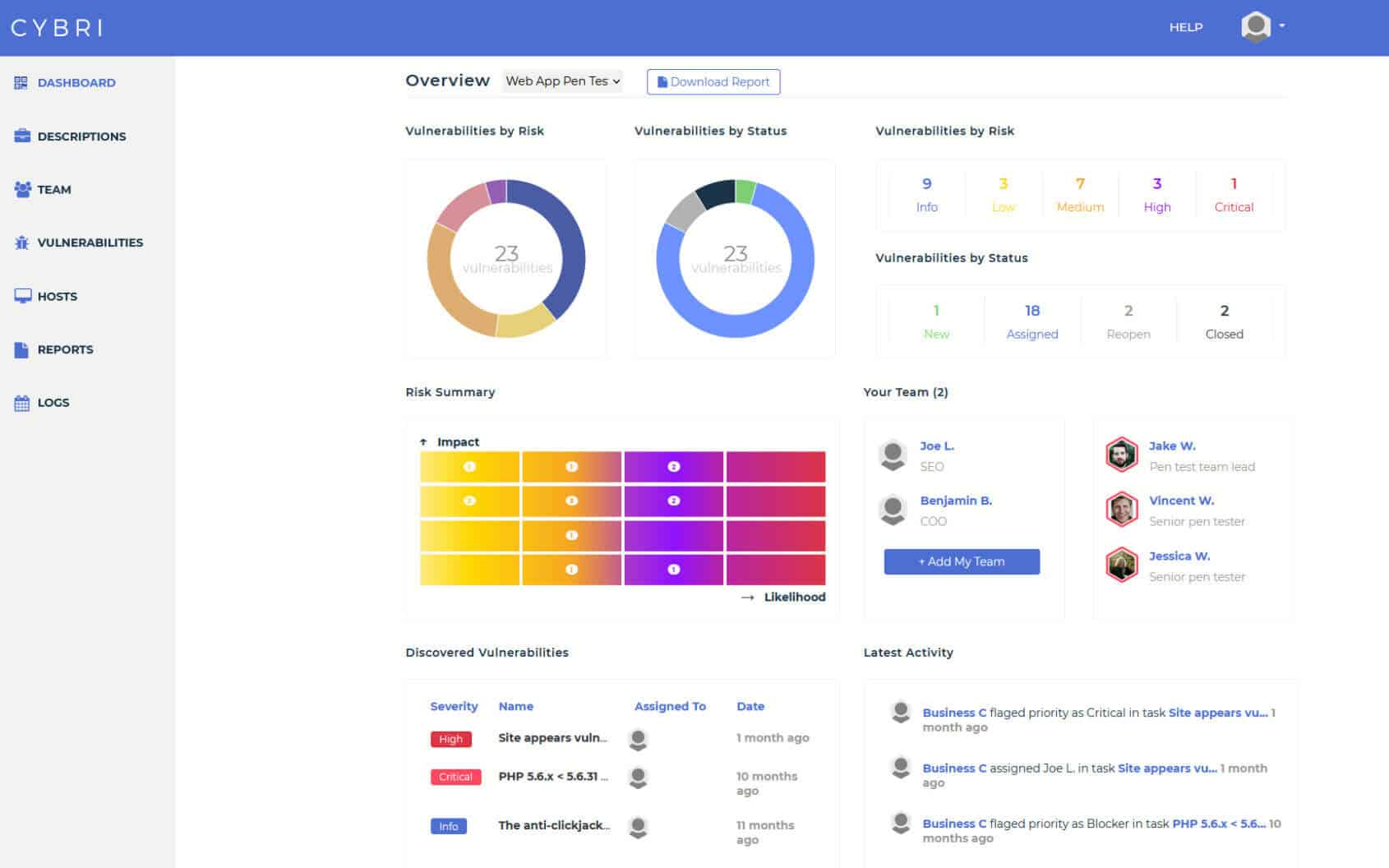
BlueBox Dashboard & Reporting
Easy access to clean and concise reports that can be shared among your executive and technical teams.
Transparent Process
We value visibility and transparency. Use our cloud-based platform to follow the pen testing progress and take action as our team detects new vulnerabilities.
CYBRI Penetration Testing Service
The CYBRI Red Team provides the best penetration testing services to top industry and technology leaders. We perform custom penetration tests on your infrastructure. CYBRI’s transparent process, security program and manual testing will give you the utmost technical assurance and let you focus on your growing business without any worries. We provide detailed and easy-to-understand reports with a comprehensive framework that will keep you updated on all the findings, ensure you get the proper guidance to strengthen your security with the appropriate level of effort needed to remediate the findings.
Assets we test
Web App
Mobile App
Network & Infrastructure
Cloud
API
What Sets Us Apart
To be one of the best penetration testing service providers we created our own data-centric results delivery platform, Blue Box. Blue Box helps you stay on track when it comes to testing and detecting critical vulnerabilities. Blue Box’s simple dashboard and team collaboration function help you maintain results with the highest level of accuracy, security, and organization. We provide a detailed description and proof of concept for each finding as well as an actionable remediation plan.
CYBRI Red Team (CRT)
- U.S.-based
- Vulnerability delivery platform
- Penetration Testing as a Service

What makes CYBRI one of the Premier penetration testing company
CYBRI has spent years to become one of the top penetration testing service providers by vetting the best experts in the US. That ensures your company is working with the top pen testers in the country and have a top-of-the-line penetration and application assessment methodology.
CYBRI takes pride in its exceptional customer service and is devoted to providing our clients with the best automatic and manual penetration testing services to help them improve their cybersecurity posture.
Penetration Testing Compliance
How CYBRI Penetration Testing Works
Discovery
We will collect the needed information from you and your team to make sure that the right assets are being tested and the right team is assigned.
RED TEAM IN ACTION
CYBRI Red Team members will start testing your infrastructure and will ensure coverage of OWASP top 10 vulnerabilities. They will utilize their own techniques to ensure the highest levels and standards of testing.
Reporting
Collaboration
After each finding is verified by our Red Team members, they get submitted into your dashboard and report. Upon completion of each test, you will have a clear report that can be shared with executive and technical members as well as your clients.
Retest
Once the findings have been remediated by your team and the time is right to retest your technology, you can easily do so by scheduling a new test with us or by purchasing an annual package of multiple tests.
Repeat
Improve risk posture and decrease the liability of your organization. Asses the cybersecurity and risk of your organization on an annual engagement basis with the top five percent of the nation’s cybersecurity talent, the CYBRI Red Team.
We spend a week or more preparing before we execute. We will collect the needed information from you and your team to make sure that the right assets are being tested and the right team is assigned.
CYBRI Red Team members will start testing your infrastructure and will ensure coverage of OWASP top 10 vulnerabilities. They will utilize their own techniques to ensure the highest levels and standards of testing.
Communicate with CYBRI Red Team members about your vulnerabilities and assign the vulnerabilities for remediation to your team members; all directly in our platform. Our platform has a clear collaboration functionality to help your team with remediation of the findings.
After each finding is verified by our Red Team members, they get submitted into your dashboard and report. Upon completion of each test, you will have a clear report that can be shared with executive and technical members as well as your clients.
Once the findings have been remediated by your team and the time is right to retest your technology, you can easily do so by scheduling a new test with us or by purchasing an annual package of multiple tests.
Improve risk posture and decrease the liability of your organization. Asses the cybersecurity and risk of your organization on an annual engagement basis with the top five percent of the nation’s cybersecurity talent, the CYBRI Red Team.
What is penetration testing?
Penetration testing or pentest is a controlled simulated cyberattack on your network or a target application (Mobile, API, Apps) and Web-based applications. Pen tests are used to assess a company’s ability to defend against a cyber-attack and identify security weaknesses.
Once security weaknesses are detected they can be reduced or eliminated before bad actors discover them. A common example for why a company would need a pen test is to protect intellectual property or to ensure compliance requirements are being met.
What Are Penetration Testing Services
The goal with pen testing services is to have security professionals approach security systems and act as a determined attacker for a threat assessment. Companies that manage sensitive data or have large infrastructures are common targets for attacks from cybercriminals, so the efficiency and effectiveness of their protection technologies and tactics are extremely important.
Here are some of the things that will be tested, used, and evaluated:
- Incident response capabilities
- Web applications
- Network vulnerabilities and risks
- Security challenges
- Risk management
- Network security
- Website and Data security
- Information security
- Common security vulnerabilities
- Attack surface (or attack vectors)
- Source code and IP address
- Cyber security risk
- Common security issues
- Security gaps
- Network infrastructure
- Web vulnerability
- Endpoint security
- Web vulnerabilities
- Cross-site scripting
- Cookies
- Defenses
Methodologies & Scope
Cybri’s Penetration Testing methodology starts with initial pen tester meetings between the Red Team security experts and the client’s internal team to establish a well-defined scope and communication chain. After the scope is defined, the next phase is a vulnerability assessment during which the threat landscape is mapped. We will then crack any gathered credentials and exploit all exploitable vulnerabilities. Throughout the testing, clients will have access to all discoveries and can ask questions at any time. After the completion of the testing, there will be a question and answer session to help the internal team understand and mitigate the vulnerabilities.
Methodology
- Pre-Engagement Walkthrough
- Passive and Active Intelligence Gathering
- Vulnerability Assessments
- Credential Harvesting and Cracking
- (Optional) Exploitation and Privilege Escalation
- Speciality Testing (Bluetooth, Wireless, HVAC and IoT Control System(s), Physical)
- Reporting and Documentation (Constantly Updated and Visible)
- Post-Test Review
- (Optional) Remediation and Retesting

Scope
- Defined to IPs, URLs, and limited infrastructure by client
- Test is announced to the CYBRI Red Team
- Identify and verify vulnerabilities
- Identify default and misconfigurations
- Identify weaknesses

CYBRI Video Series On Penetration Testing
Sign up for CYBRI's Newsletter
News & Resources
Schedule a personalized demo with CYBRI.
Don't wait, reputation damages & data breaches could be costly.








Discuss Your Project