CYBRI - Premier Penetration Testing Company
Headquartered in New York, CYBRI is a leading cybersecurity and penetration testing company in the US that provides protection from cyber threats for your organization.
Our penetration testing firm delivers elite penetration testing services and provides solutions to help our customers become more protected in the ever-growing cyber threat world. We help identify and remediate mission-critical vulnerabilities that might otherwise cost your company millions of dollars if exposed by hackers.
Trusted by Top Industry Leaders
CYBRI works with companies that are leaders in their industry. CYBRI’s customers understand the importance of penetration testing services to detect security threats – pen tests are vital to their cybersecurity posture.


Benefits of working with CYBRI
U.S.-Based Red Team
All CYBRI Red Team members are U.S.-based, experienced, and highly certified penetration testers.
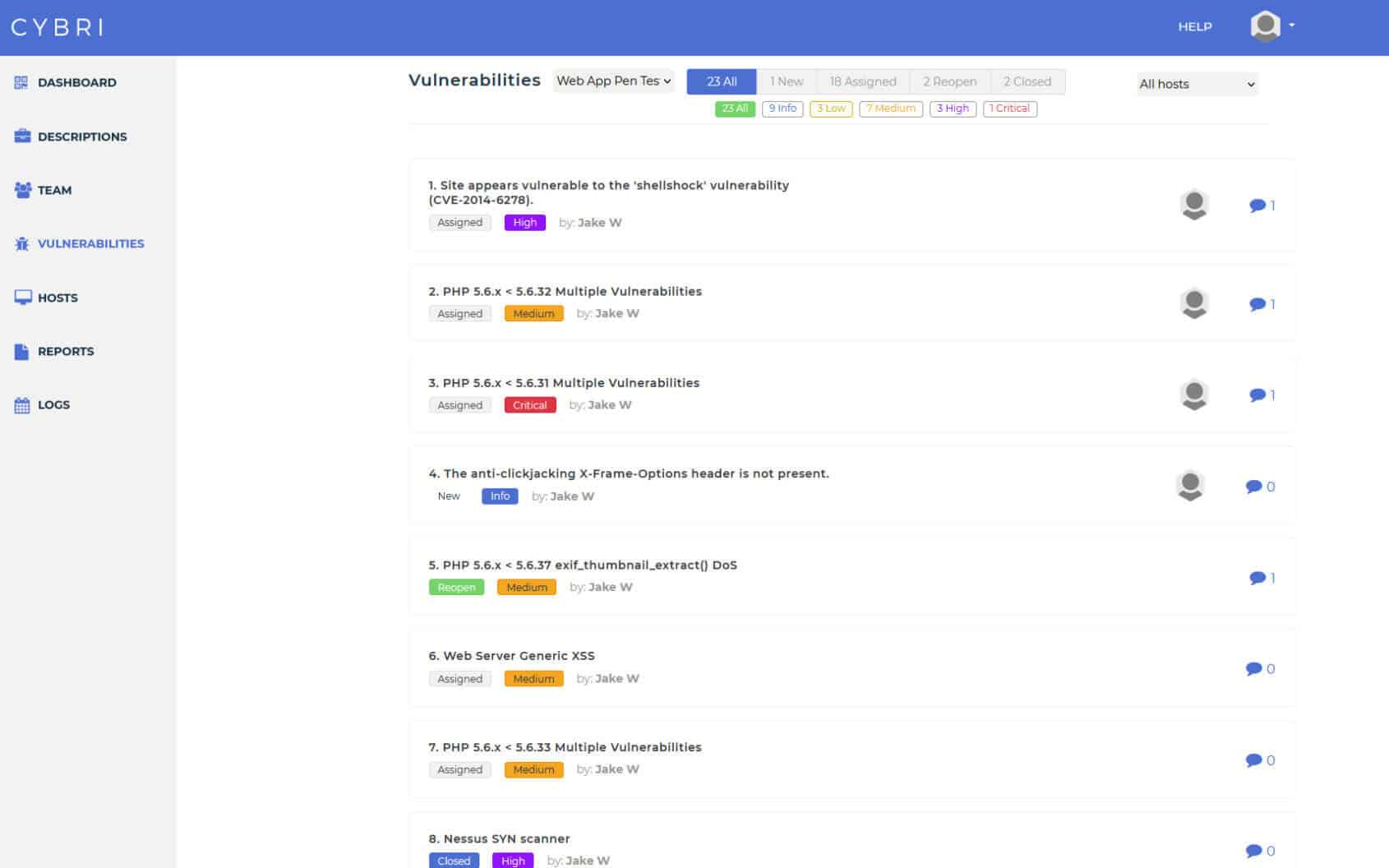
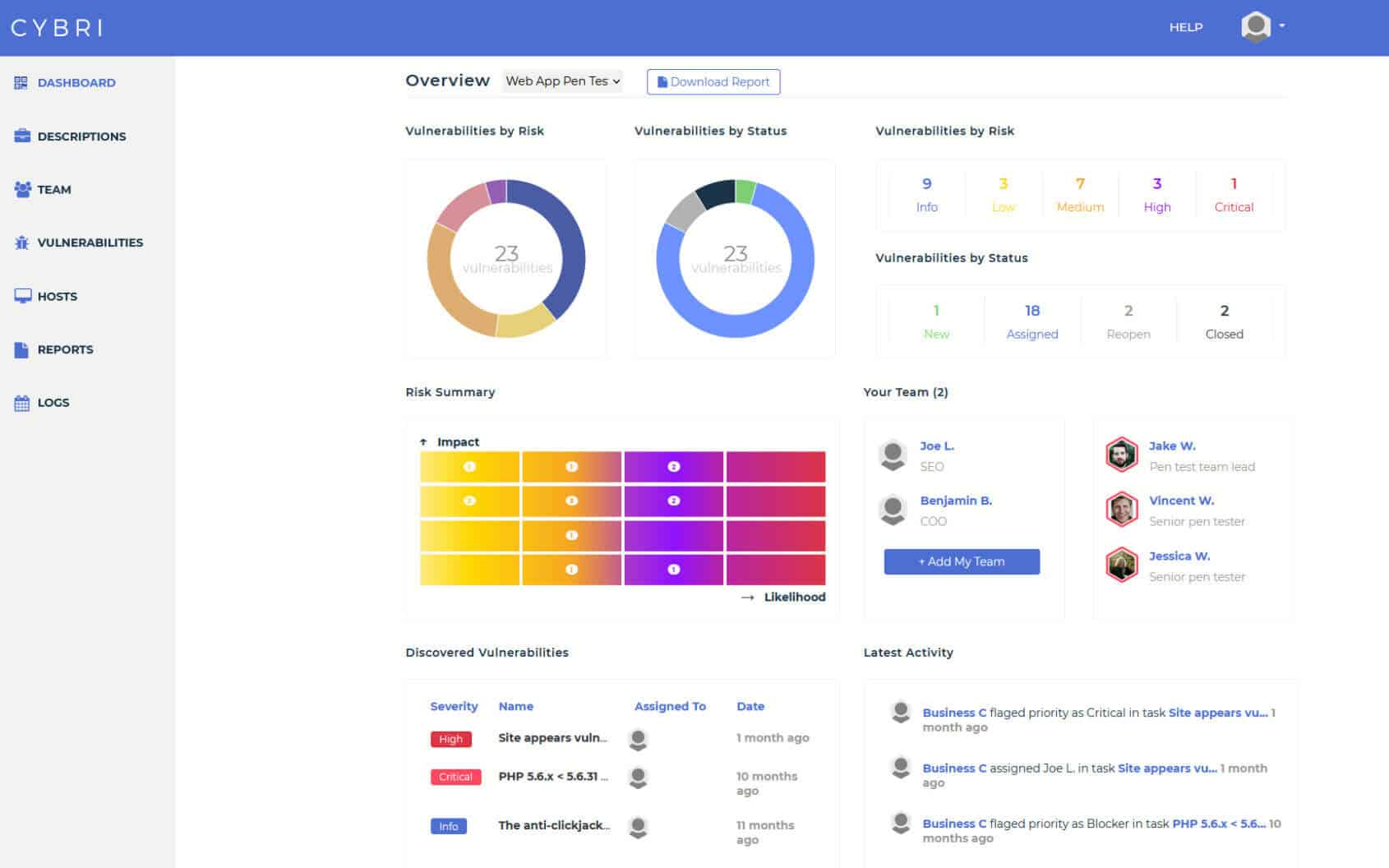
BlueBox Dashboard & Reporting
Penetration testing services with access to clean and concise reports that can be shared among your executive and technical teams.
Transparent Process
We value visibility and transparency. Use our cloud-based platform to follow the pen testing progress and take action as our team detects new vulnerabilities.
CYBRI Red Team (CRT)
We are backed up by Cybri Red Team (CRT) to help you achieve military-grade protection. Cybri Red Team are the best ethical hackers who can dig out deep-rooted vulnerabilities in your web apps, cloud apps, mobile apps, network penetration testing, servers, IoT devices vulnerability assessment, and more.
CRT members are all US-based and are leading experts with the most recognized certifications such as OSCP, GIAC, CISSP, and CEH. Some of them even carry experience from the US government, military, and Fortune companies.
What makes CYBRI one of the Premier penetration testing companies
Our outstanding top penetration testing services have attracted several clients that range from small startups to huge multinational companies thanks to our ability to identify vulnerabilities. We are dedicated to improving cybersecurity across the board, which means that our services to your organization continue even after the penetration test report has been delivered.
No matter the size of your organization, our security experts will assess all of your cybersecurity needs from scratch to provide security measures tailored to your business needs. Our experts are always available to all of our clients in an advisory capacity should you wish to contact us.
Assets we test
Web App
Mobile App
Network & Infrastructure
Cloud
API
What Sets Us Apart
How CYBRI Penetration Testing Services Work
Discovery
We will collect the needed information from you and your team to make sure that the right assets are being tested and the right team is assigned.
RED TEAM IN ACTION
CYBRI Red Team members will start testing your infrastructure and will ensure coverage of OWASP top 10 vulnerabilities. They will utilize their own techniques to ensure the highest levels and standards of testing.
Reporting
Collaboration
After each finding is verified by our Red Team members, they get submitted into your dashboard and report. Upon completion of each test, you will have a clear report that can be shared with executive and technical members as well as your clients.
Retest
Once the findings have been remediated by your team and the time is right to retest your technology, you can easily do so by scheduling a new test with us or by purchasing an annual package of multiple tests.
Repeat
Improve risk posture and decrease the liability of your organization. Asses the cybersecurity and risk of your organization on an annual engagement basis with the top five percent of the nation’s cybersecurity talent, the CYBRI Red Team.
We spend a week or more preparing before we execute. We will collect the needed information from you and your team to make sure that the right assets are being tested and the right team is assigned.
CYBRI Red Team members will start testing your infrastructure and will ensure coverage of OWASP top 10 vulnerabilities. They will utilize their own techniques to ensure the highest levels and standards of testing.
Communicate with CYBRI Red Team members about your vulnerabilities and assign the vulnerabilities for remediation to your team members; all directly in our platform. Our platform has a clear collaboration functionality to help your team with remediation of the findings.
After each finding is verified by our Red Team members, they get submitted into your dashboard and report. Upon completion of each test, you will have a clear report that can be shared with executive and technical members as well as your clients.
Once the findings have been remediated by your team and the time is right to retest your technology, you can easily do so by scheduling a new test with us or by purchasing an annual package of multiple tests.
Improve risk posture and decrease the liability of your organization. Asses the cybersecurity and risk of your organization on an annual engagement basis with the top five percent of the nation’s cybersecurity talent, the CYBRI Red Team.
What is pen testing?
Penetration testing, or pen test is a controlled simulated cyberattack on your network or applications (Mobile, API, Apps). Pen tests are used to assess a companies’ ability to defend against a cyber-attack and identify security weaknesses.
Once security weaknesses are detected they can be reduced or eliminated before bad actors discover them. A common example of why a company would need penetration testing services is to protect intellectual property or to ensure compliance requirements are being met.
About Us

Schedule a personalized demo with CYBRI.
Don't wait, reputation damages & data breaches could be costly.








Discuss your Project