Web Application Penetration Testing Services
Cyber attacks on applications have spiked dramatically. Hackers target web applications with the specific goal of stealing sensitive information and disrupting business operations.
CYBRI’s web application penetration testing services cover all aspects of your app, from user roles, API and mobile integrations, infrastructure, business logic, and. We ensure that each new feature release maintains a strong cybersecurity posture by scheduling your monthly and quarterly pen tests with our easy-to-use BlueBox platform.
What Is Web Application Penetration Testing?
Web applications interact with your system data and are often the targets for hacking attempts given their online nature. Web app pen testing can be a complex process as it involves a wide range of variables, differing system architectures, and coding language specific parameters.
Benefits Of Working With CYBRI
Work with the nation’s top web app pen testing experts to detect vulnerabilities before hackers do.
U.S.-Based Red Team
All CYBRI Red Team members are U.S.-based, experienced, and highly certified web application penetration testers.
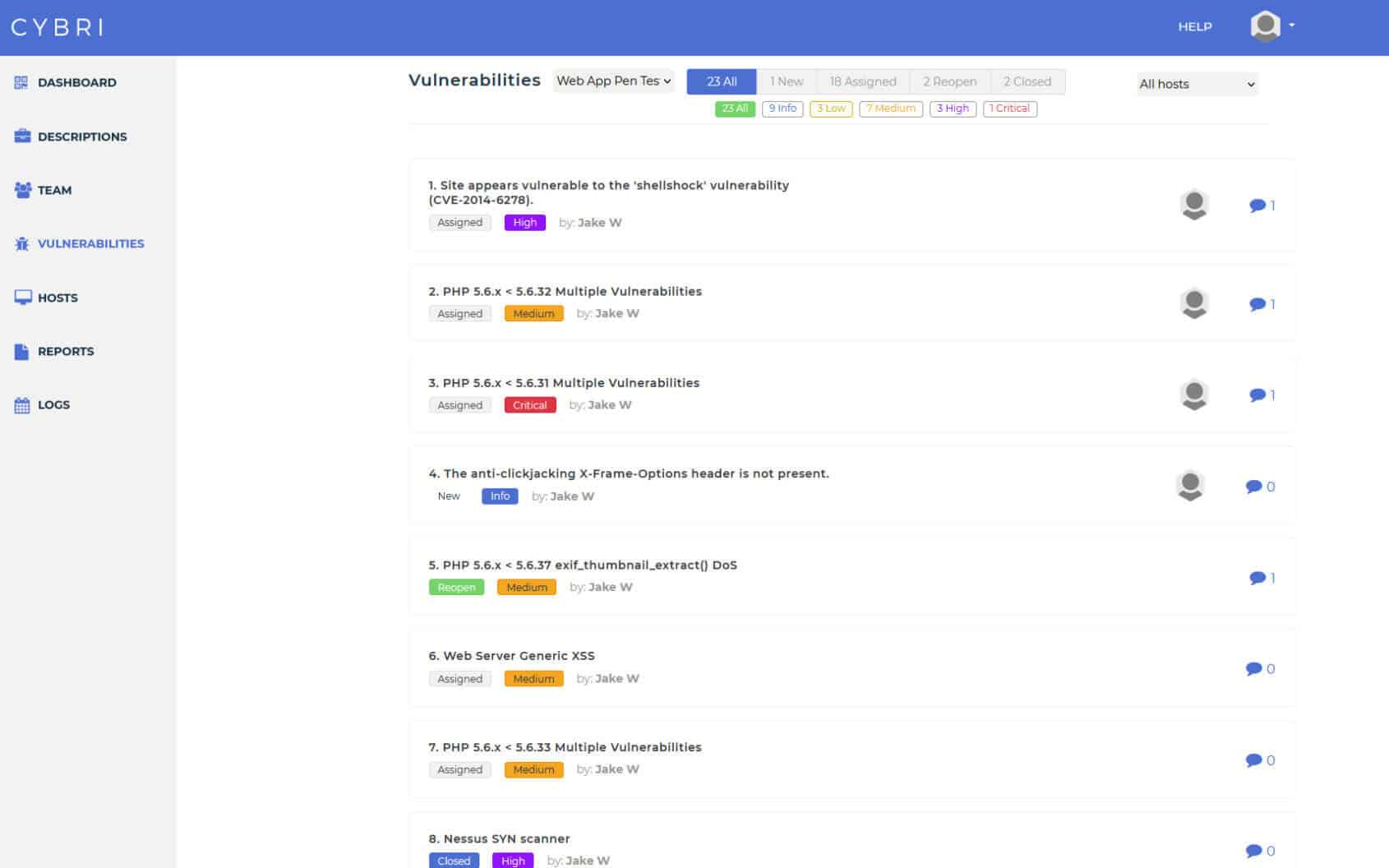
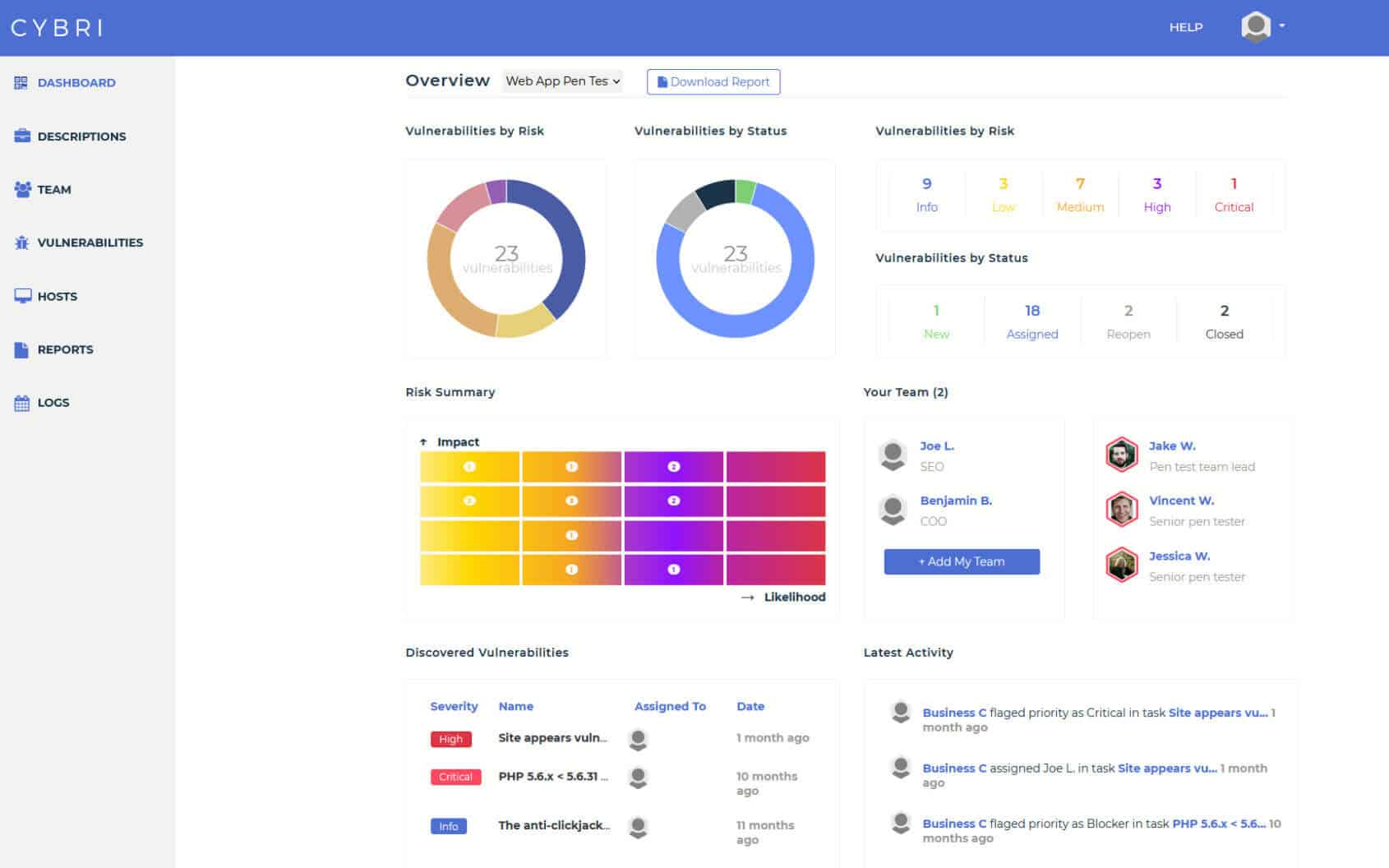
BlueBox Dashboard & Reporting
Easy access to clean and concise web application penetration testing reports that can be shared among your executive and technical teams.
Transparent Process
We value visibility and transparency. Use our cloud-based platform to follow the web application penetration testing progress and take action as our team detects new vulnerabilities.
Maximizing Value Of Web Application Penetration Testing
User Role/Authenticated Testing
We perform a thorough penetration test on your web application from every aspect and each user role using OWASP ASVS, which also includes looking for the OWASP Top 10. This works best for agile teams who update app features frequently.
Mobile
API
API testing is often done in conjunction with web penetration tests. APIs can be a weak vector into any organization that doesn’t check its security. We leverage OWASP’s research to find the most common attack vectors.
Cloud
Your web application sits on top of infrastructure, and even it is in the cloud, it is important to test. Our experts have deep experience in all major cloud providers and follow their terms of service to ensure no interruption: AWS, GCP, Azure, and Oracle. This gives you the opportunity to dive deep into your application’s infrastructure.
Code Review
Black Box/Unauthenticated Testing
Agile Pen Testing
What Our Customers Have to Say








Why You Need It:
- Functionality releases – Ensure each release of your application is secure as they get released, as opposed to waiting. Get tested before your release goes public.
- Compliance - Whether you need to comply with SOC2, HIPAA, PCI-DSS, or other standards, getting a pen test will help you meet those requirements.
- Vendor/Customer Requests - Customers and vendors may require you to perform an application penetration testing to ensure you are secure and showcase that your organization takes the necessary measurements to protect their data. Using our methodology based on OWASP ASVS, OSSTMM, and PTES, we can give them confidence in the results of your test.
- Security Awareness - Pen testing your application will ensure you know where you stand in comparison to industry standards and get the peace of mind you need, such as knowing you have no vulnerabilities in the OWASP Top 10.
- Intrusion Prevention - Application pen testing can reduce your attack surface, which significantly reduces the likelihood of compromise.
The Attack Vectors We Test:
- Broken Access Control where the validation of access does not properly validate all conditions and can allow access to areas where the user was not meant to go or allows for privilege escalation.
- Cryptographic Failures is a common problem where the protocols and cipher suites that are used are insecure, or that secure communication channels can be bypassed.
- Injection includes any ability to have inputs process data improperly, namely to be run as a line of code. This includes the very common and famous SQL injections and Cross-site scripting vulnerabilities.
- Insecure Design is a new focus, different from insecure implementation, where the flaw is logical and often rooted in the application's code structure and not a specific vulnerability with a patch. These require more intensive testing and remediation.
- Security Misconfiguration features many basic problems that are still left by the application designers. This includes default passwords, unnecessary features, overly verbose errors, default or lack of security controls.
- Vulnerable and Outdated Components are probably the most commonly known attack vector, as these can be easily found by a scanner. The importance of testing is to ensure that these findings are legitimate and do not impact other components. This can include third-party tools, libraries, packages, and programs.
- Identification and Authentication Failures is also a commonly found weakness, where the authentication itself is insecure. This can be the allowance of brute-forcing, weak password requirements, insecure password change systems, or exposure of authentication details such as session tokens.
- Software and Data Integrity Failures are when the data is exposed and does not have sufficient validation of its integrity, allowing attackers to be able to modify it unbeknownst to the owners. This can be caused from an insecure CI/CD pipeline, allowing for malicious code or access. This includes supply chain compromise
- Security Logging and Monitoring Failures is not often covered by a pen test but usually falls within a secure configuration review. Logging is often a too little, too late problem where victims don’t know they didn’t have it until something bad happens.
- Server-Side Request Forgery is not a common attack vector, but it is gaining in popularity. Thi is often when a web application is fetching an unvalidated remote resource, and that is subject to redirection to a malicious server. This can bypass a firewall, WAF, or other protection.
What Makes CYBRI One Of The Premier Web App Penetration Testing Companies
Our outstanding web application penetration testing company has attracted several clients that range from small startups to huge multinational companies. We are dedicated to improving web app penetration testing and cybersecurity across the board, which means that our services to your organization continue even after the web app penetration testing report has been delivered.
No matter the size of your organization or web application, we will assess all of your cybersecurity needs from scratch to provide security measures tailored to your web app business needs. Our experts are always available to all of our clients in an advisory capacity should you wish to contact us.
What To Expect During An App Pen Testing:
- Elite services from US-based security experts, who have specialized certifications and expertise in applications
- Hands-on professional advice from our experts to answer your questions and concerns to get the most out of your testing experience
- An expert report that comes in multiple versions for you to distribute appropriately, from an executive summary for management, to a technical report for the developers, or a compliance focused attestation; our clean reports are exactly what you need.
Assessments
What Sets Our Web App Penetration Testing Apart
Use our proprietary BlueBox platform to collaborate with CYBRI’s highly qualified US-based web app Red Team to detect critical vulnerabilities, sensitive data leaks, increase remediation, and access pen test results as they are discovered.
How CYBRI Penetration Testing Works
CYBRI web application penetration testing processes are on-demand hacker-powered penetration tests performed by one or two Red Team members. You pay a fixed price for your test and we do the rest. You can always increase the frequency.
Discovery
We will collect the needed information from you and your team to make sure that the right assets are being tested and the right team is assigned.
RED TEAM IN ACTION
CYBRI Red Team members will start testing your infrastructure and will ensure coverage of OWASP top 10 vulnerabilities. They will utilize their own techniques to ensure the highest levels and standards of testing.
Reporting
Collaboration
After each finding is verified by our Red Team members, they get submitted into your dashboard and report. Upon completion of each test, you will have a clear report that can be shared with executive and technical members as well as your clients.
Retest
Once the findings have been remediated by your team and the time is right to retest your technology, you can easily do so by scheduling a new test with us or by purchasing an annual package of multiple tests.
Repeat
Improve risk posture and decrease the liability of your organization. Asses the cybersecurity and risk of your organization on an annual engagement basis with the top five percent of the nation’s cybersecurity talent, the CYBRI Red Team.
We spend a week or more preparing before we execute. We will collect the needed information from you and your team to make sure that the right assets are being tested and the right team is assigned.
CYBRI Red Team members will start testing your infrastructure and will ensure coverage of OWASP top 10 vulnerabilities. They will utilize their own techniques to ensure the highest levels and standards of testing.
Communicate with CYBRI Red Team members about your vulnerabilities and assign the vulnerabilities for remediation to your team members; all directly in our platform. Our platform has a clear collaboration functionality to help your team with remediation of the findings.
After each finding is verified by our Red Team members, they get submitted into your dashboard and report. Upon completion of each test, you will have a clear report that can be shared with executive and technical members as well as your clients.
Once the findings have been remediated by your team and the time is right to retest your technology, you can easily do so by scheduling a new test with us or by purchasing an annual package of multiple tests.
Improve risk posture and decrease the liability of your organization. Asses the cybersecurity and risk of your organization on an annual engagement basis with the top five percent of the nation’s cybersecurity talent, the CYBRI Red Team.
Schedule a personalized demo with CYBRI.
Don't wait, reputation damages & data breaches could be costly.








Discuss Your Project